Blog

Login – Who am I?
by Business Analysis (BAPL). What is authenticity? What is authentic? I once read a paper that described two different perspectives of authenticity. The first being how true is something to

Access Requests and Entitlements
by Business Analysis (BAPL). When my youngest daughter Tams turned 18, she was ready to hit the clubs in the city. This had been a long time coming and she

Identity Lifecycle Management
by Business Analysis (BAPL). “At Facebook, we build tools to help people connect with the people they want and share what they want, and by doing this we are extending
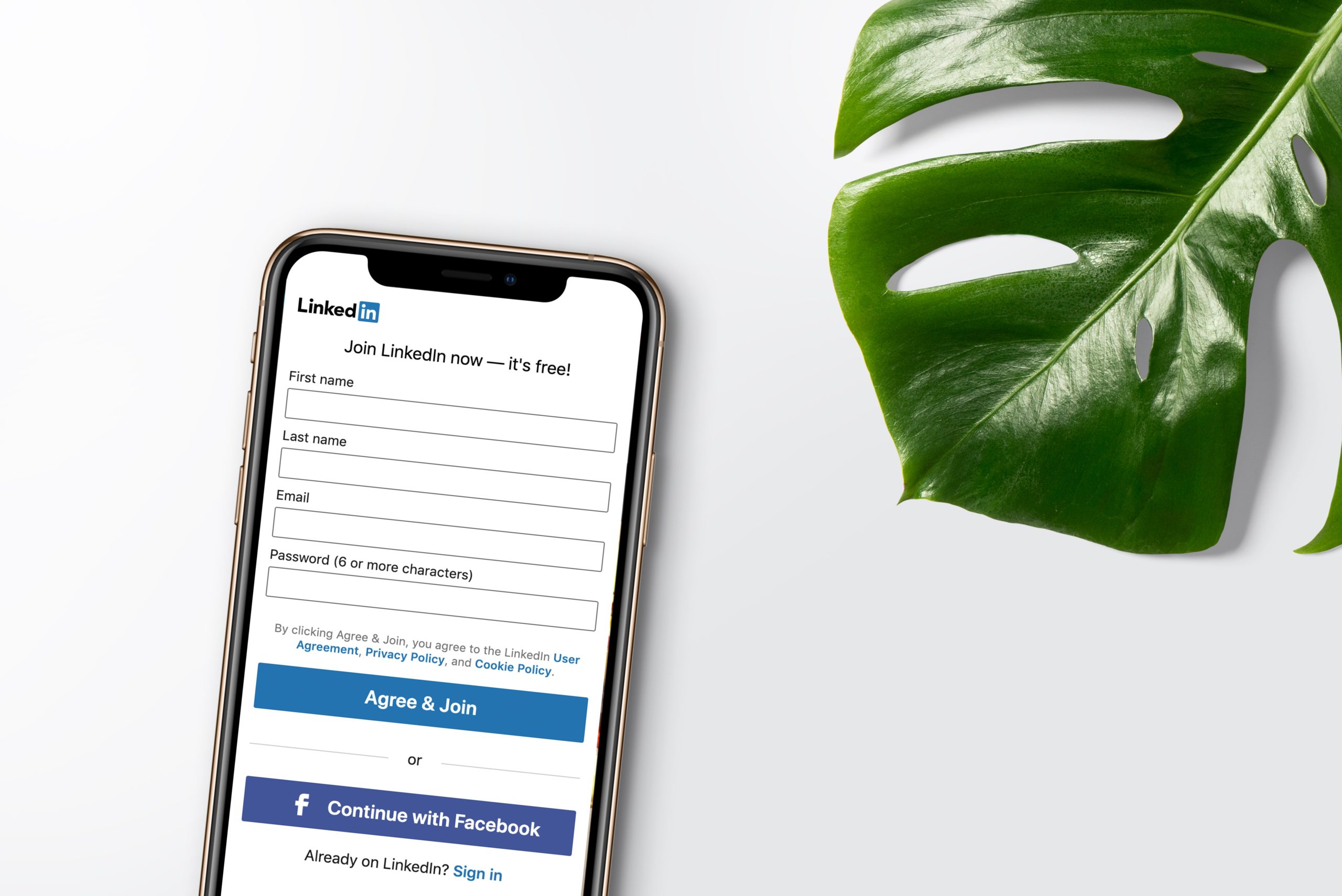
Registering a New Account
by Business Analysis (BAPL). Recently my partner’s daughter (Lucy) said she had an invitation to a gender reveal party. Unfortunately, I come from a day long gone when gender reveal

Introduction to the IAM Processes
by Business Analysis (BAPL). There seems to be a lot of attention on Identity information and in particular identity theft recently. With the increasing rate of data breaches targeting Personal

CRM and Scrum
by Business Analysis (BAPL) The transition to Agile for Dynamics 365 or CRM methods is revolutionising enterprise software projects. Agile projects offer faster deployments, reduced costs, higher quality, more satisfied